Random notes and recipes you may find helpful
Anonymous I2P proxy
This is pretty handy if you want to blog about democracy from China or do security research on the I2P darkweb (which by default usually dumps out onto the regular internet via a TOR exit)
Below are the steps I carried out on ‘minibian’ for a raspberry pi, which should work similarly on any Debian based distro. It is assumed that you have a freshly installed operating system using a static ip in your DMZ…
#### Run below commands as root
passwd root
apt-get update
apt-get dist-upgrade
apt-get install oracle-java8-jdk
apt-get install nano htop
adduser user2
nano /etc/apt/sources.list
#### Add these lines then save
deb http://deb.i2p2.no/ jessie main
deb-src http://deb.i2p2.no/ jessie main
#### control+x to save
wget https://geti2p.net/_static/i2p-debian-repo.key.asc
apt-key add i2p-debian-repo.key.asc
apt-get update
apt-get install i2p i2p-keyring
i2prouter start
nano /home/user2/i2pstart.sh
#### Add these lines
#!/bin/bash
i2prouter start
#### control+x to save
chmod u+x /home/user2/i2pstart.sh
#### Run below commands as user2
crontab -e
#### Add these lines then save
0 * * * * /home/user2/i2pstart.sh
@reboot /home/user2/i2pstart.sh
#### Run below commands as user2
nano /home/user2/.i2p/i2ptunnel.config
#### Change these lines from
tunnel.0.interface=127.0.0.1
tunnel.6.interface=127.0.0.1
#### to
tunnel.0.interface=0.0.0.0
tunnel.6.interface=0.0.0.0
#### Run below commands as root
reboot
Now forward a high UDP and TCP port to the box from your firewall
I2P is now running and accessible from a browser if the proxy is setup, I recommend setting up a separate browser just for this, like firefox portable since you can set proxy independent of system.
Setup proxy to use port 4444, then navigate to your box in a web browser from another machine.
Scroll to bottom of UI and go to Bandwidth settings.
Mine is setup for 512KBps In & 256KBps Out with Share of 80%, you may want to go lower but these settings give me great performance. (Note big B for Byte, this is actually 4Mbit Down & 2Mbit up).
Go to the network tab, specify the high UDP and TCP ports you forwarded earlier from your firewall.
Once you save the left-hand status pane should show ‘Network: OK’
#### All done!
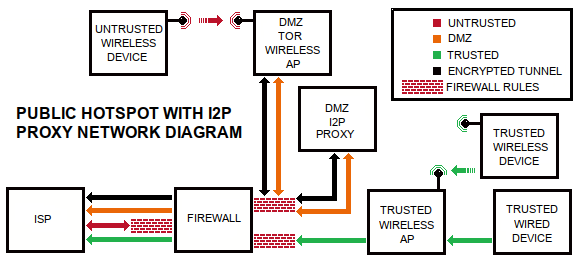
‘Worry free’ public hotspot
Many moons ago, my daughter came to me with an interesting challenge: her gameboy only supported WEP. I wasn’t willing to create an insecure wireless network based on WEP, but after some thought, it occurred to me that I could create a wide open network for public to connect to, not a whole lot different from a coffee shop, without any authentication. Why not take this approach?
Here are some good reasons:
1) You could be held responsible for activities carried out on your internet connection, P2P filesharing is a good example. For this reason also, coffee shops usually have a splash page with rules you must agree to before using.
2) You would not want your traffic impeded by users of the hotspot
To solve problem #1 you can prevent user traffic from being attributed to your public IP address by using the TOR protocol. TOR is normally intended for anonymity, it was originally developed by the US Navy. By sending the untrusted user traffic to TOR, it gets redirected somewhere else in the world, and access to the internet happens from somewhere else in the world vs your WAN IP address as it would normally. Anonymity that TOR provides will be destroyed by users that are signing into services like Facebook (as they would on any public hotspot), so nevermind that feature of TOR for this purpose. A really easy way direct the traffic into TOR is to use an OpenWRT based firmware called Gargoyle that has built-in transparent TOR proxy out of the box, this will block non-TOR protocols, ensuring that only TOR traffic goes out of your WAN IP. It works on several routers, even on a PC if you do not have a supported router. Just install, enable TOR for all traffic, block unsupported protocols, and make sure its connected to your DMZ network segment.
To solve problem#2 your main router should be using QoS feature of your router, and you would want to designate only leftover bandwidth to go to (and come from) this device, ensuring your normal traffic is the priority.
Having a public hotspot I can turn on when needed prevents me from having to give my main wifi password to guests to get them on the internet. It’s not super fast but YouTube videos play. There is one undesirable side effect: Google shows a different page to people based on source IP, and coming off of a random TOR exit somewhere else in the world, Google may be Google Japan or Google Canada from time to time, but other than that the hotspot users will be be oblivious to using TOR. There is a way to set a specific exit node if you need it to be a predictable TOR exit every time.
Additional recommendations:
Setup periodic reboot as a keepalive
Only access TOR proxy from WAN side with https and SSH
Install watchcat to reboot if connectivity is lost with main firewall via ping
Assume TOR could fail open and block p2p protocols on this subnet
Block .onion sites, remember anonymity is not functional for this purpose
NoDogSplash can be used to intercept the first webpage visited with splash webpage of your choosing, can use that to let the public know what rules you have for your hotspot
QEMU Notes
#### MAKE DRIVE
qemu-img create /mnt/usbdrive/vm/os.img 5G
#### INSTALL OS
qemu -vnc :1 -hda /mnt/THUMBDRIVE/VM/OS.IMG -cpu host,+x2apic -cdrom /mnt/THUMBDRIVE/VM/fix.iso -m 1024 -net nic -boot d -usbdevice tablet &
##### RUN OS
qemu -vnc :1 -hda /mnt/usbdrive/vm/os.img -cpu host,+x2apic -smp 3 -m 2048 -daemonize -net nic -net bridge,br=green0 -boot c -usbdevice tablet &
#### WINDOWS EXAMPLE
C:\Progra~1\qemu\q64.exe -L -kernel-kqemu -hda d:\VM\android.img -cdrom D:\VM\android7.iso -m 2048 -net user -net nic,model=rtl8139 -soundhw es1370
SETI@Home (headless) on Linux
##### DEBIAN 10
ADD THIS TO /etc/default/grub, MODIFYING THIS LINE FROM
GRUB_CMDLINE_LINUX_DEFAULT=”quiet”
#### TO
GRUB_CMDLINE_LINUX_DEFAULT=”quiet vsyscall=emulate”
update grub
reboot
apt-get install boinc-client
#### USE YOUR OWN ACCT KEY HERE , GET FROM WEBSITE
boinccmd –project_attach http://setiathome.berkeley.edu 12345__678910111213
service boinc-client stop
nano /var/lib/boinc-client/global_prefs_override.xml
#### ADD THIS IN BETWEEN GLOBAL PREFERENCES, MODIFYING AS YOU NEED
<global_preferences>
<run_on_batteries>1</run_on_batteries><run_if_user_active>1</run_if_user_active><run_gpu_if_user_active>1</run_gpu_if_user_active><suspend_cpu_usage>75.000000</suspend_cpu_usage><leave_apps_in_memory>1</leave_apps_in_memory><max_ncpus_pct>75.000000</max_ncpus_pct><cpu_usage_limit>75.000000</cpu_usage_limit>
</global_preferences>
service boinc-client start
boinccmd –get_simple_gui_info
DONE!
####### COPY FILE VIA SCP
scp myfile.txt remoteuser@remoteserver:/remote/folder/
##### Fix original Ooma inability to connect due to non-existent DNS server
iptables -t nat -I PREROUTING -d 208.83.244.20 -j DNAT –to-destination 8.8.8.8
##########INTENTIONAL UNDERCLOCK (FOR LOUD FANS / EXCESSIVE HEAT)
cpupower frequency-set –max 800000
(VERIFY WITH)
cat /sys/devices/system/cpu/cpufreq/policy0/cpuinfo_cur_freq
#######WRITE ISO TO SD CARD
dd if=file.iso of=/dev/sdX status=progress
########DISABLE IPV6 ON DEBIAN
nano /etc/sysctl.d/disable-ipv6.conf
—–ADD THIS TO FILE AND SAVE:——
net.ipv6.conf.all.disable_ipv6=1
——APPLY——
sysctl -p -f /etc/sysctl.d/disable-ipv6.conf
—–CONFIRM NO inet6———
ip a
########PLAY MP4 ON ANCIENT VIDEOCARD
mpv –vo=x11 –hwdec=no –framedrop=vo –cache=yes –cache-secs=10 –audio-delay=0.3 yourfile.mp4